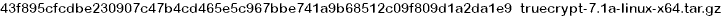
It is a frequently expressed view among computer security experts that information security must "just work", hidden from the view and requiring no end user's understanding or knowledge.
This is a fallacy.
Without good understanding of the fundamentals, a user will invariably make some seemingly trivial error that will, unknown to him, completely subvert the security of the system. Without knowledge of the fundamentals, it is impossible to differentiate between trivial and significant issues, or between minor and critical errors. Does this matter? It depends on the circumstances, but one thing is certain: without such knowledge the participation in any activity that requires a high level of digital security is, at best, imprudent.
Security requirements depend greatly on the value of the confidential information, on the technical capabilities of the adversary and on the cost in time, effort and discipline that an owner is prepared to invest in order to protect his or her data or communications. Collectively, the definition of these factors is known as the threat model. A software tool or a protocol that is a reasonable solution for one threat model might be totally inadequate for another.
This selection of links includes many service providers that claim to unreservedly protect their user/customer confidentiality and privacy. However, not only are they all unable to resist legal coercion of their domestic jurisdictions, they are invariably subject to commercial corruption, where the motivation and resources is directly proportional to their size and market share. Consequently, before putting any degree of trust into such claims, it is well worth reviewing two widely‑publicized examples of how such trust could be misplaced; the first one from the ancient era of cryptography dominated by electro‑mechanical devices and "numbers" radio stations, the second from the contemporary landscape of ubiquitous mobile telephony: CryptoAG Corporation and Phantom Secure incidents.
What follows is therefore not a set of magic bullets, but a list of tools and learning resources that are more often than not worth consulting.
Posteo: E‑mail service
One of the few e‑mail services that works well in POP mode, therefore
a first choice of those that are not prepared to use web‑mail. It's
SMTP connection accepts subscriber's outgoing mail regardless of how
they are connected to the 'net and what the From: message header is.
This makes it work well with Spamgourmet (see below). The cost is reasonable
(1 € per month as of Q3/2021) and it accepts anonymous payments. In conjunction
with Thunderbird's OpenPGP implementation, probably the easiest way to set
up encrypted communication where the private keys are generated and known to
be kept securely nowhere but on the end user's computer.
Thunderbird: E‑mail client emeritus
Free, open-source e‑mail client available for Linux, MS Windows and MacOS.
Since late 2020 (v. 78 and on) Thunderbird includes native OpenPGP public
key encryption. Wisely, the developers decided to abandon the entire
"Web-of-Trust" infrastructure, the most serious impediment to wider adoption
of PGP e‑mail encryption for the past two decades. With Thunderbird
"profile directory" on a removable encrypted medium (see below, TrueCrypt -
or similar) properly configured and carefully operated on a Linux computer is
probably the most secure e‑mail communication within the reach of an
individual with no professional computer security assistance. Their FAQ
promises implementation of "hidden recipient" (i.e., absence of e‑mail
address in the public key and recipient's Key ID in the encrypted
message) which is the main missing feature required for better protection
against the ubiquitous mass surveillance. There is an extensive
practical guide to e‑mail encryption using Thunderbird.
Spamgourmet: E‑mail re-direction and spam protection
If you give your email address to everyone, you are bound to receive spam
emails, and you won't know where they came from. This long-lived service is
one of the most convenient and effective anti-spam and e‑mail privacy-enhancing
tools on the 'net. Spamgourmet provides a number of domains from which the
forwarded traffic appears to be - helpful for by-passing filtering by
services which are doing what they can to prevent the use "e‑mail protection"
techniques.
AnonAddy: Another E‑mail re-direction service
Similar and complementary to Spamgourmet. Specifically, more suitable for
list subscription and persistent communication channels with cooperating
correspondents. Unlike Spamgourmet, it provides a paid-for
service level with a number of additional features. However, even the free
level makes possible the encryption of forwarded traffic, so the user can
protect the content snooping by those that have the cooperation of his ISP.
Duckduckgo Search Engine: no tracking, no ad targeting,
just searching
"We don’t store your search history. We therefore have nothing
to sell to advertisers that track you across the Internet."
DuckDuckGo web site includes useful privacy tips in form of
a "product Blog".
KeePassXC password manager
KeePassXC is an open source, cross platform, light graphical interface program
that saves many different types of information e.g. user names, passwords,
urls, attachments and comments in one single encrypted database, protected
by a password and/or key-files.
Encryption Wizard file and folder encryption software
Simple, strong, Java-based file and folder encryption software for protection
of sensitive information. Without requiring a formal installation or elevated
privileges, EW runs on Microsoft Windows, Mac OS X, Linux, Solaris, and many
other operating systems. (Note, 2022: Encryption Wizard "umbrella project"
appears to have entered a dormant stage, cf:
https://distrowatch.com/table.php?distribution=tens - but the archives of
the application can still be found on the 'net. After downloading,
verify the sha256 hash of the file:
bf2663dd2ce5d0513d4a556d81398a2eee9415039b650e0208eca404a984056d
EncryptionWizard-Public-3.5.9.zip
36b35dad67dd3ba39052ae7d72878ef85096049c84e2c7981a9fb4067f3db398
EncryptionWizard-Unified-3.5.10-FIPS.zip )
Wormhole file and folder exchange service
Browser based, very simple to use, but the security of the shared content
depends entirely on the method by which the retrieval URL is made known
to the recipient. Passing the URL via open e‑mail must be avoided if there
is any possibility of active e‑mail surveillance, but e‑mails archived
beyond the server retention period (at the time of this writing only 24
hours) will not reveal the content. A reasonably secure method is to
share the URL via desktop Signal messaging application.
Notex: a different approach to encrypted email
Notex, a program similar to Windows Notepad, exchanges encrypted or decrypted
text with any POP mail-client program or (if you are using web‑mail) the browser,
via the clipboard. It is quite unorthodox in that it uses single secret key that
both the sender and recipient must exchange via a personal contact or a trusted
channel. While this requires some effort, the communication is extremely
resistant to the e‑mail content surveillance commonly performed with the
cooperation of Internet service providers and/or mail service providers, or by
exploiting SSL Internet infrastructure weaknesses. It requires no special
installation and works on all versions of Windows and on Linux
via Wine.
TrueCrypt: encrypt data on your computer; Wikipedia article
Now abandoned by the original developers, this open source freeware utility performs
what is known as "on-the-fly" encryption. It can create a virtual "encrypted disk"
within a file, or encrypt a partition so that a user can have disk-resident data safe
from an adversary who has stolen or sequestered his computer while the device was
powered down. (System partition encryption capability of TrueCrypt should be avoided).
While the development has been discontinued some years ago, it is still
considered safe to use. Search the 'net for truecrypt-7.1a-linux-x64.tar.gz
file, download it and verify its sha256 hash:
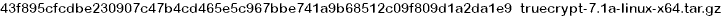
ProtonMail: free, encrypted Web‑mail service
For those that are prepared to trust the owner/operator of some
web‑mail service with both the content of their e‑mail communications
and the storage of their encryption keys, Proton mail is the first
one among those to consider - but only after absorbing the lesson of the
Crypto AG case mentioned in the introduction of this text.
Proton‑mail offers a (somewhat pricey) paid-for service tier with many useful features, but even their "free" service provides a very good level of privacy-protection:
Signal: a messaging application for "smart phones"
Best of the bad lot among messaging applications for mobile devices
(i.e., Android/Google and iOS/Apple).
The assumption that communication can be secured on devices de-facto owned by hardware and operating system vendors and communication service providers is debatable at best. This application, at least, has open source, and can (on Android only) be "side-loaded" from an application install bundle provided directly by the developers. The source device code has been reviewed by independent information security experts, but the server code and security protocols are not available for independent scrutiny.
Signal's user-id is the mobile telephone number and, in an attempt to gain mobile messaging market share, Signal owners broadcast the time any user has joined the service to all that have their telephone number in the device contact manager - this fact makes it trivial to compose the lists of users and their Signal id's. To their credit (but after an almost ten‑year delay from the first mention of it) in 2024/Q1 Signal implemented user‑selectable addresses (erroneously called "usernames"). While a telephone number is still the account identifier (known to the application owner/developer!), this feature makes it somewhat practical to protect the user's identity from opportunistic attackers. Since this a new feature, some time will be required to confirm its claimed security benefits.
As of 2020/Q2, Signal has substantially downgraded the trustworthiness of the service by storing user's profile data and contact list on their servers. While it is claimed it is stored in a secure manner, that claim is somewhat "thin" and impossible to independently verify.
As mentioned in the introduction, no messaging application on Google/Apple mobile device should be considered "secure". Anybody using Signal in circumstances that require more than the basic level of protection from "opportunistic snooping" should consult the following guide.
Jami: a decentralized cross-platform text, voice and video
messaging application.
A relatively recent application, with (so far)
small user-base. It provides only peer-to-peer messaging, thus it is of any
utility for those with "always on" computer. (Always-on mobile device is
unlikely to be a prectical solution for a user with even a very modest privacy
requirements). However, looking at other specifications, it is superior to
its competitors on all principal criteria: it requires no phone number or
e-mail for account generation, it is free to use for anybody, it is open
source and peer-to-peer. The account identifier is a derivative (hash) of
its public key: by far the most robust manner in which to implement asymmetric
cryptography based communication system. The user name is optional, and
the only information that is kept "in the Cloud" is the association between
the unique, short name-string and the account id. Single account can be used
on multiple devices. By far the most important characteristic of Jumi is that
it is a peer-to-peer application: it requires no central server for users
with changing IP numbers to find each other on the Internet. If nothing
else, this will prevents the "Signal-effect": the gradual weakening of the
trust that was initially afforded the system owner/operator.
GrapheneOS: A private and secure mobile OS
Graphene is an open source Android variant for Google's Pixel family of
mobile telephones.
GrapheneOS is the most successful example of last of the above three categories. Given the fact that the most egregious invasion of user's privacy happens at the application software layer that either exploits the holes in the OS or cooperates with it for mutual benefit of device vendor and application owner/operator, replacing the commodity device's OS with a "better (software) mousetrap" has undeniable merit.
GrapheneOS developers have made a sensible decision to develop, test and support their operating system on only a single family of reasonably priced, good-quality mass-market hardware devices (Goggle's Pixel). Unfortunately, the "entry-treshold" is too high for an average mobile telephony user. Making the installation (and reverting the device back to vedor's original condition) simple enough for the "non-technical" user is what would be required to recommend GrapheneOS to all those insisting on using mobile devices but at the same time looking for a reasonable level of privacy and a modicum of communication security.
Electronic Frontier Foundation: the leading nonprofit
organization defending civil liberties
Learning resource: not complete, not error-less, but a good place to start
learning about the privacy and information security landscape. The link
above leads directly to their "Tips, Tools and How-tos for Safer On-line
Communications" web page, but the rest of the web site is also well-worth
visiting.
The Call of the Open Sidewalk: Bruce Walzer's excellent
wiki-site on all things PGP
Refreshingly un-ortodox collection of articles on the subject. One of the best
sources on the Internet of in-depth knowledge of PGP. (see below, "PGP at 30).
Of all the text on the site, one sentence is especially worth repeating:
"I believe that reliability and security are best achieved with simple systems.
OpenPGP is a standard that describes such a system". The sentence (and
the text of the article) explains why any secure communication requires good
software engineering at least as much as good mathematical cryptography.
Arch Linux Wiki: An excellent resource for all things Linux
Arch is probably the best‑documented Linux distribution, and its insistence
on simplicity makes it a good choice for the OS of a security‑centerd PC.
The Wiki units of specific interest in present context are those on
GnuPG,
Data-at-rest_encryption,
Stateless OpenPGP, and probably the best annotated
List of Linux security applications on the Internet.
Zeltser's blog article
"How Digital Certificates Are Used and Misused"
Trusting that "padlock" icon on the browser URL address line? This article
explains why it is probably okay to trust it with low-value Internet commerce
transactions, but not much more than that.
E‑mail security:
a short overview.
An introduction to the subject for those with little or nor previous
knowledge of it.
Schneier on Security: Blog by Bruce Schneier
Schneier is author of many books, most notably "Applied Cryptography - Protocols,
Algorithms, and Source Code in C". His newsletter ("Crypto-Gram") provides monthly
e‑mail summary of the events and developments in the field of cryptography and
information security.
Financial Cryptography: "Where the crypto rubber meets the Road
of Finance..."
Another expert-level blog, focusing on the information security of financial
systems.
Freedom to Tinker: "digital technologies in
public life..."
This Princeton University's Center for Information Technology Policy
web publication is a bit wider in its scope than other collections of
texts linked to here, but the quality of the content published makes
it worthy of regular visits.
Financial Cryptography: "Where the crypto rubber meets the Road
of Finance..."
Another expert-level blog, focusing on the information security of financial
systems.
Zdziarski's blog article "Protecting Your Data at a Border
Crossing"
Learning resource, an overview of issues surrounding inspection of digital
devices by various Customs and Immigration agencies. The rest of the blog
is interesting, but often at the information security expert level.
Tor: software and an open network that defends against traffic
analysis
The Tor network is a group of volunteer-operated servers that allows people to
improve their privacy and security on the Internet. Note however that extremely
aggressive surveillance techniques, normally used only against specific, high-value
targets can break Tor. Additionally, Tor slows down the network traffic to a degree
that makes it unsuitable for high-volume applications.
Tails, a live operating system that can be run from a USB stick
or a DVD
Tails is a complete operating system designed to be used from a USB stick or a
DVD independently of the computer's original operating system, in order to preserve
user's privacy and anonymity. It helps one to use the Internet anonymously and
circumvent censorship almost anywhere you go and on any computer but leaving no
trace unless you ask it to explicitly.
Burp: clean cypher-text file encryption utility
File encryption utility that produces encrypted file that consists entirely of
a random data stream - it can not be easily detected or "provably identified" as
cipher-text, as long as the key is secure, or unless it is broken cryptographically.
The GNU Privacy Guard (GnuPG): PGP, at thirty
Following a number of open source code forks, corporate transformations and
the introduction of OpenPGP standard, this is most widely used current
descendent of 1991 Phil Zimmermann's Pretty_Good_Privacy program.
Fundamental parts of OpenPGP standard functionality have been included in a large number of computer applications (see Thunderbird and ProtonMail, above). In contrast, GnuPG is a stand-alone program that, in theory at least, could be used by an end user to perform encryption and decryption of his "generic" messages and data files. However, it's complexity - specifically the integration of Web of trust functionality - has ensured that as a stand-alone command-line application GnuPG is a niche product, used primarily by experts and software developers/distributors. It helped little that in transition from version 1.x to 2.x, the developers made it even more difficult to use by the average computer user. (The current state of the project is an excellent example of how inadequate software engineering can erode the usefulness of a system built by excellent cryptographers).
Fortunately, the final version 1.x (1.4.23) is still included in all Linux distributions. Linux and MS Windows portable binaries can be downloaded from here.
There is no shortage of Internet resources for those with the need to use this application, such as these versions of 1.x and 2.x and concise usage summaries.
GnuPG simplified: GnuPG without the W-O-T crud
In its original form, GnuPG "public key" e‑mail encryption program is a
product of unmatched cryptographic strength, unfortunately tightly integrated
with the ill-conceived and horrendously complex W-O-T ("web-of-trust") public
key authentication scheme. In addition to the complexity which restricts its
use to a niche of devotees, W-O-T completely subverts user's privacy.
This site outlines a method for using GnuPG without the W-O-T infrastructure.
Introductory text includes an explanation of the mechanics of public key
(aka. "asymmetric") cryptography. (Note: With OpenPG implementation
in Thunderbird 78.x and on, most features of this project (except
the air-gap operation) are now available in a mainstream mail client
application).
Lord: Large Opaque Removable Device backup
In many instances (see, for example, Zdziarski's blog article above) it can
be advantageous not to store any confidential data on the laptop computer disk,
but keep it instead on an encrypted external USB flash memory "drive", which is
"mounted" only when the computer is in active use.
Such "drive" should be regularly backed up, preferably in its "opaque", i.e., encrypted state. This can be an onerous operation for large-capacity devices. This program and the accompanying documentation provides a quick and reliable method for performing such backups.
Choose the Red Pill and the Blue Pill:
A Position Paper by Ben Laurie and Abe Singer
In what can now surely be described as "long time ago..." (2006!), two
prominent computer security practitioners and authors had not only the wisdom,
but also the courage to state the obvious: "Our position is that the
general-purpose operating system is fundamentally inadequate for trusted
operations. One can have a general-purpose system or a trusted system, but
one cannot get both in a single package."
The authors propose a solution: "Have a second system with a built-secure operating system, which operates in tandem with the first. The separate device is built for the purpose of providing a trusted path, and providing a usable interface. We call this device "The Nebuchadnezzar."
A decade before the proliferation of "smart mobile telephones" and the inane "two factor authentication" protocols hinging on essentially insecure general-purpose operating systems (Android, iOS) devices and even more insecure SMS message delivery pipelines, the authors also speculate: "Mobiles come closer to the Neb's requirements, but still, they tend to be too open...". Looking at that sentence in 2024, with typical user's device loaded with large number of applications, in constant network communication with servers owned and operated by equally large number of un‑trusted application vendors, even "too open" is a glaring understatement.
The fundamental premise of the article is however even more of a truism today than it was when the article was written. The hope thus remains that at some future point in time there will exist a critical mass of e-mail correspondents and on-line service providers and their users who have come to the same conclusion. If and when this happens, the article author's "Nab" device - in some form - might become a reality.

